Microsoft Defender
Setup
Connect to your Microsoft Defender app for OAuth.
To setup your Microsoft Defender app in Cobalt for OAuth, you will need the following credentials from your Microsoft Azure account:
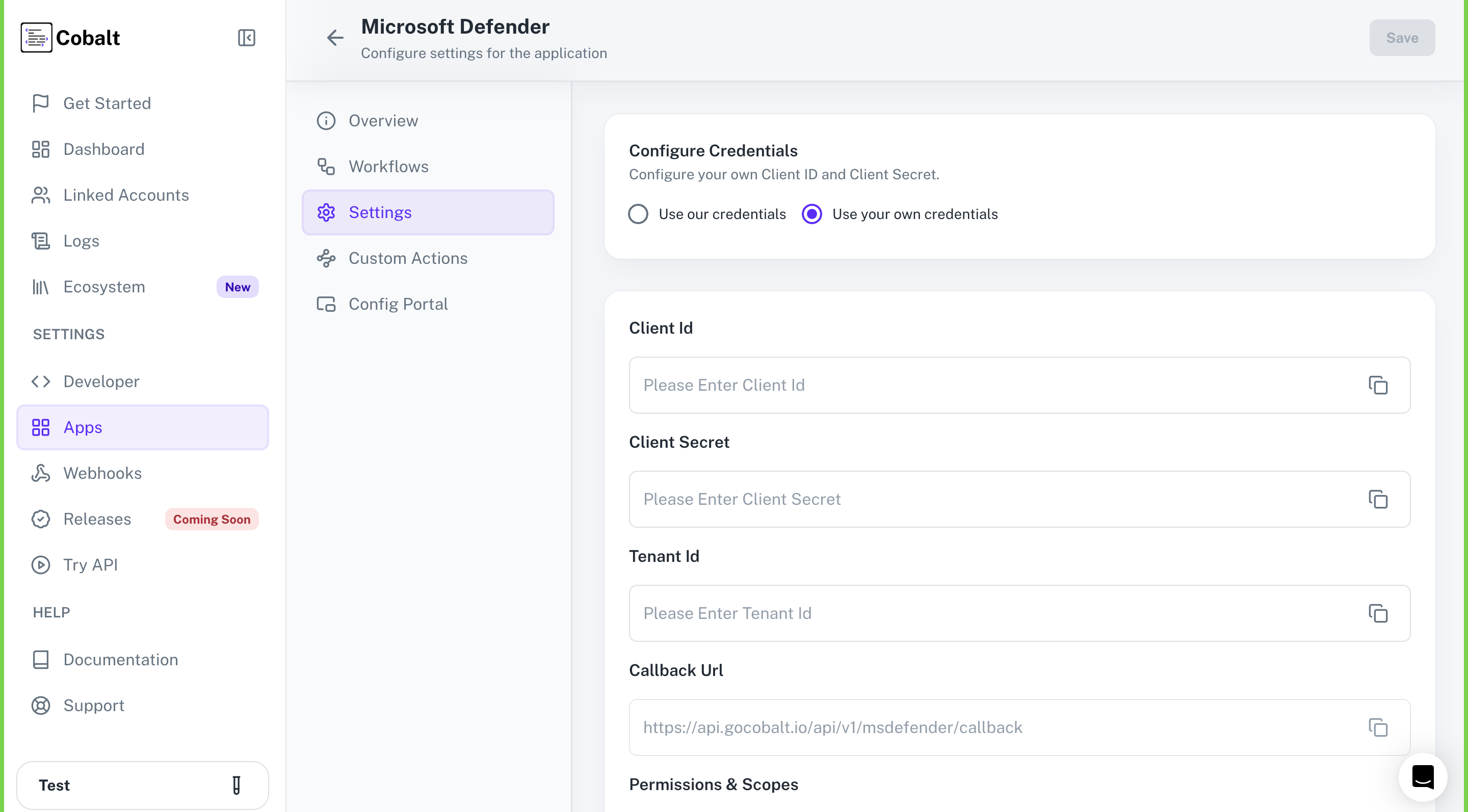 Provide the acquired Client ID and Client Secret under Settings of the app and save it.
Provide the acquired Client ID and Client Secret under Settings of the app and save it.
 Once the scopes has been added to the application in Cobalt, go to your Microsoft Azure account and update the scopes as added on Cobalt.
Select the OAuth App created for Cobalt and follow Step 8 and 9 above.
Once the scopes has been added to the application in Cobalt, go to your Microsoft Azure account and update the scopes as added on Cobalt.
Select the OAuth App created for Cobalt and follow Step 8 and 9 above.
- Client ID
- Client Secret
- Tenant ID
- Scopes
Pre-requisites
- Microsoft Azure Account. You can create one here.
Required Settings
- Mandatory Scopes
- User.Read
If you haven’t already created an app in Microsoft Azure, you’d need to create one.
Creating an app in Microsoft Azure
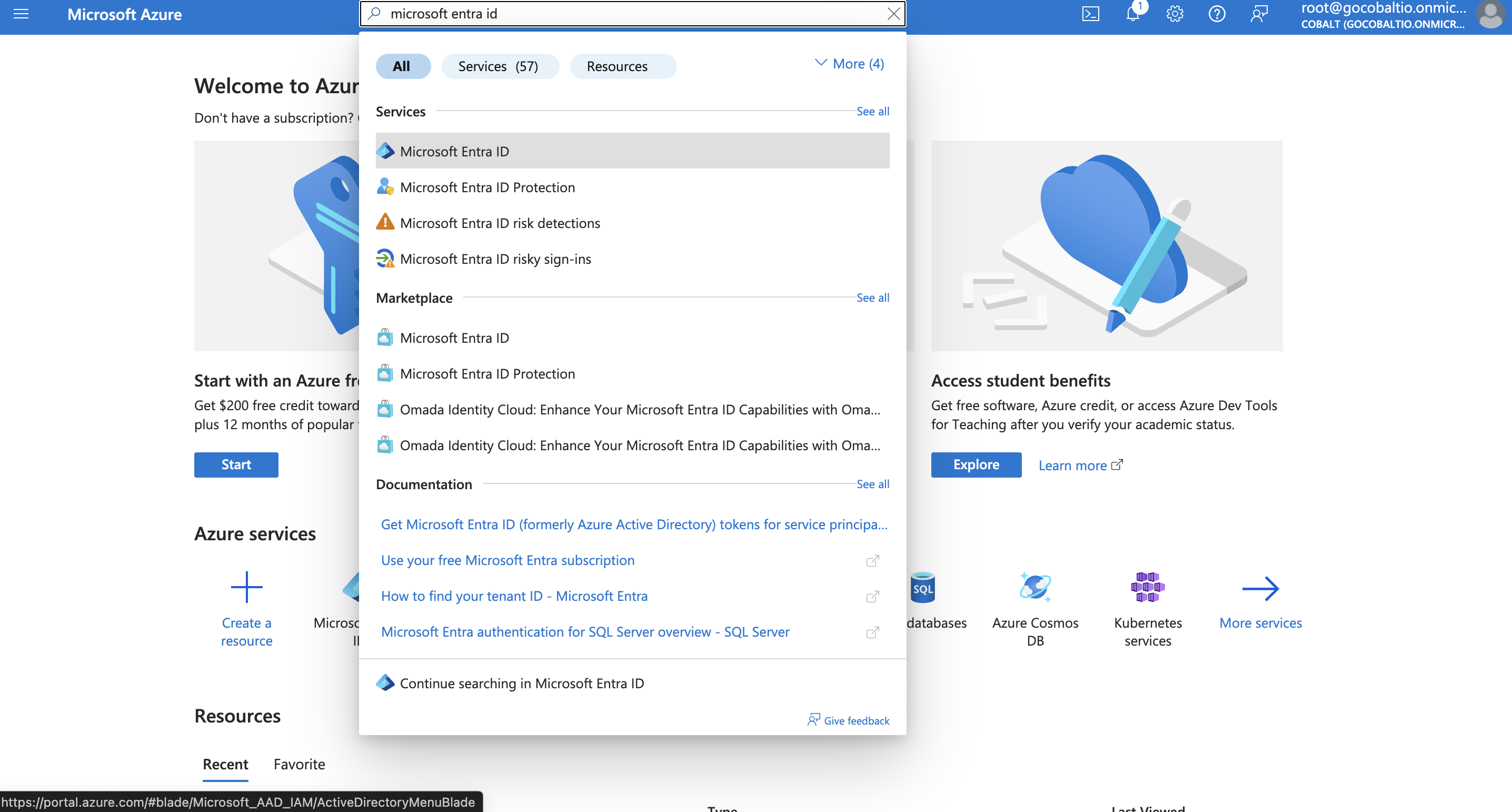
To create a Microsoft Defender app and acquire the above mentioned credentials, please follow the steps mentioned below:- Log in to your Microsoft Azure account.
- Search for Microsoft Entra ID and select it from Services in the top search bar.

- Navigate to
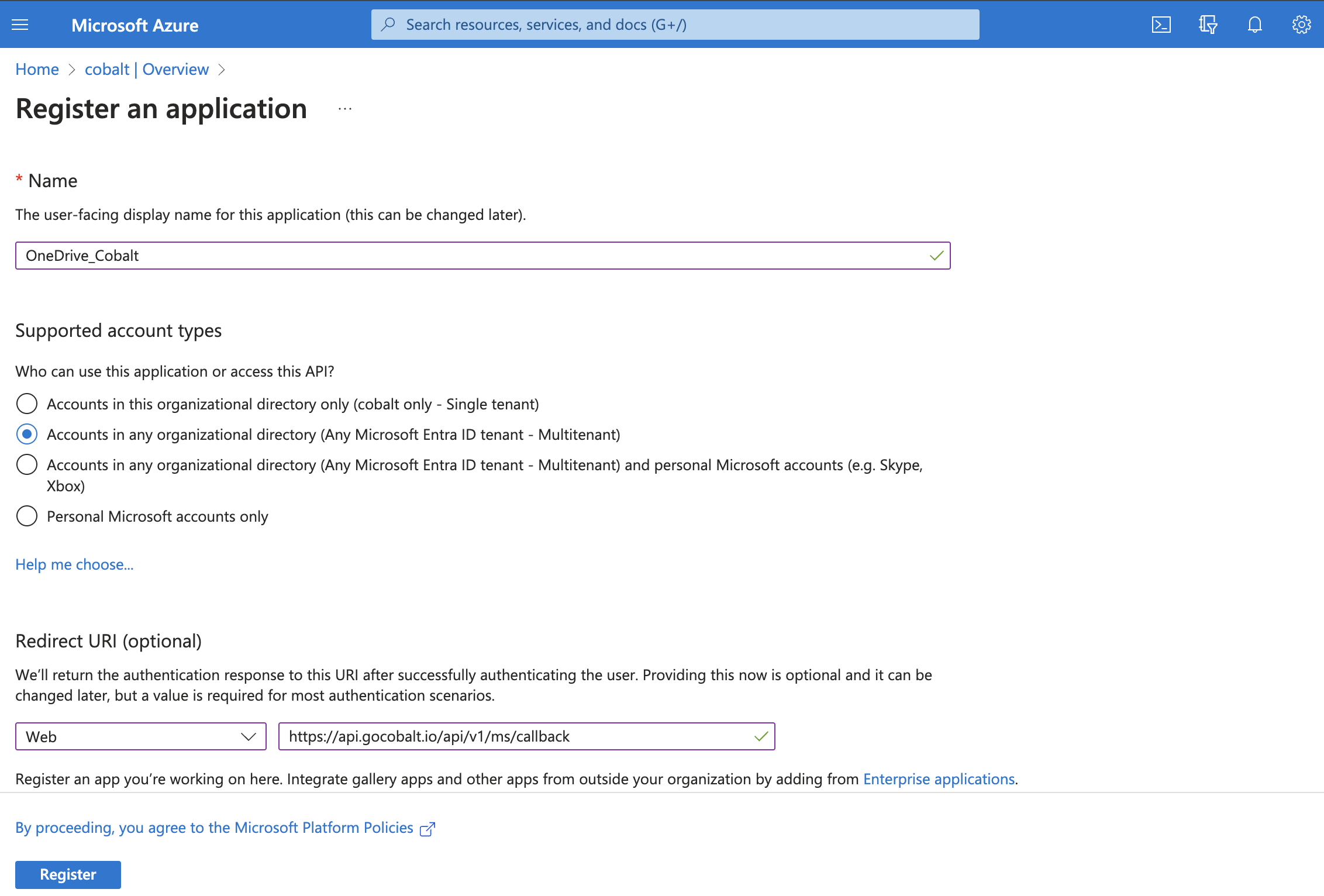
Overviewin the side menu > Click on+Add> SelectApp Registration. - Enter the App Name for your application and select
Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant)under Supported Account Types. - Go to your
Apps catalogin Cobalt > Search forMicrosoft Defender>Settings>Use your credentials>Callback Url> Copy it. - Under the Redirect URI section, select Platform as
Web, paste the Callback Url as the URL and clickRegister.

If you already have an app created, then follows these steps to add Redirect URL:Select your Application > Select Authentication in side menu > Under Platform configurations, press the Add a platform button > Select Web > Paste the Callback Url > Click on Configure > Click Save button at the bottom.
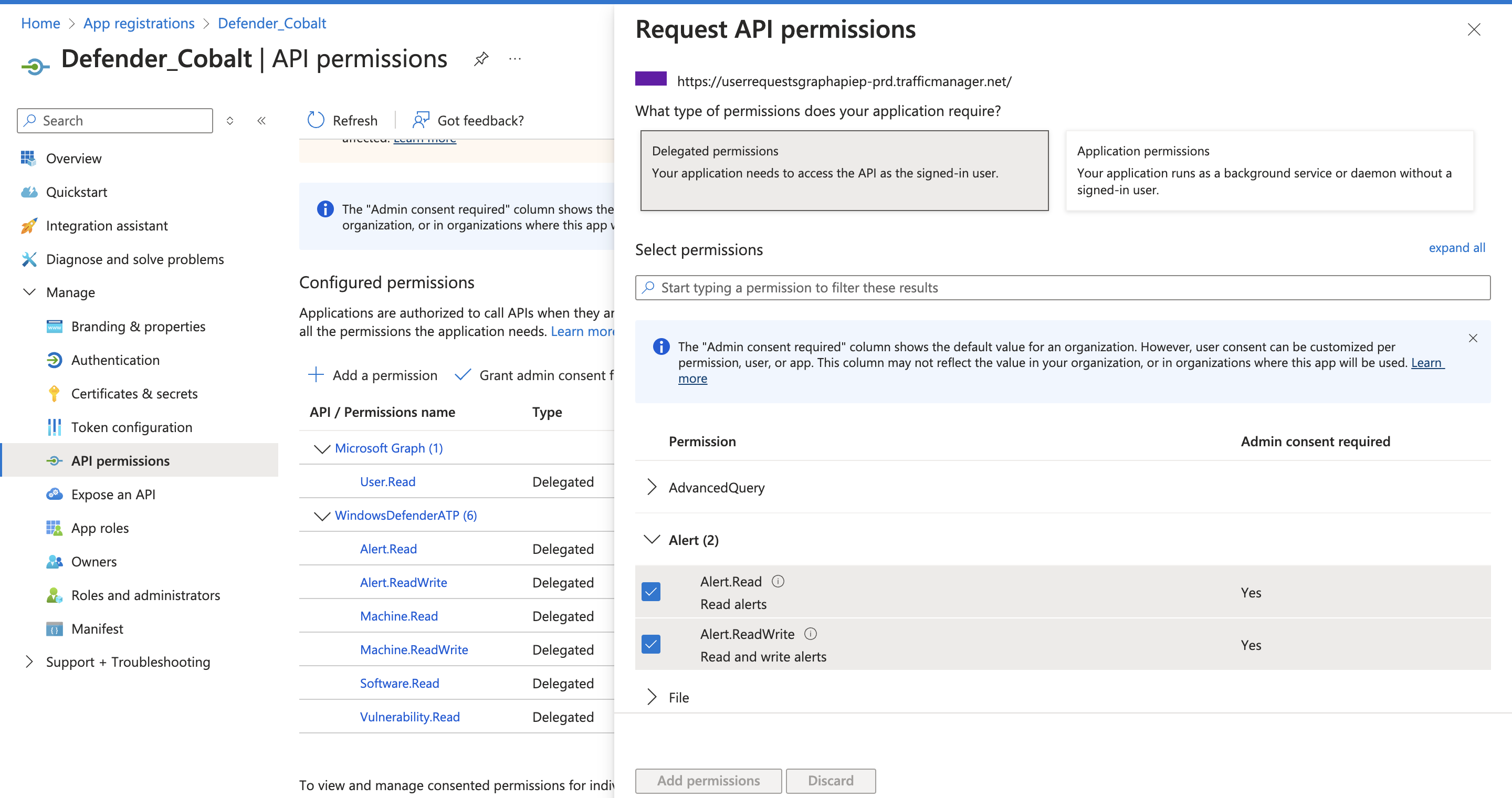
- Navigate to
Manage>API permissionsin the side menu > Click on+ Add a permission. - Choose the
Microsoft Graphcard under Microsoft APIs > ChooseApplication permissions> Select the mandatory scope > click on theAdd Permissionsbutton. - For Defender specific scopes, navigate to
APIs my organization usestab > Search forWindowsDefenderATPand choose the required scopes fromDelegated permissions.

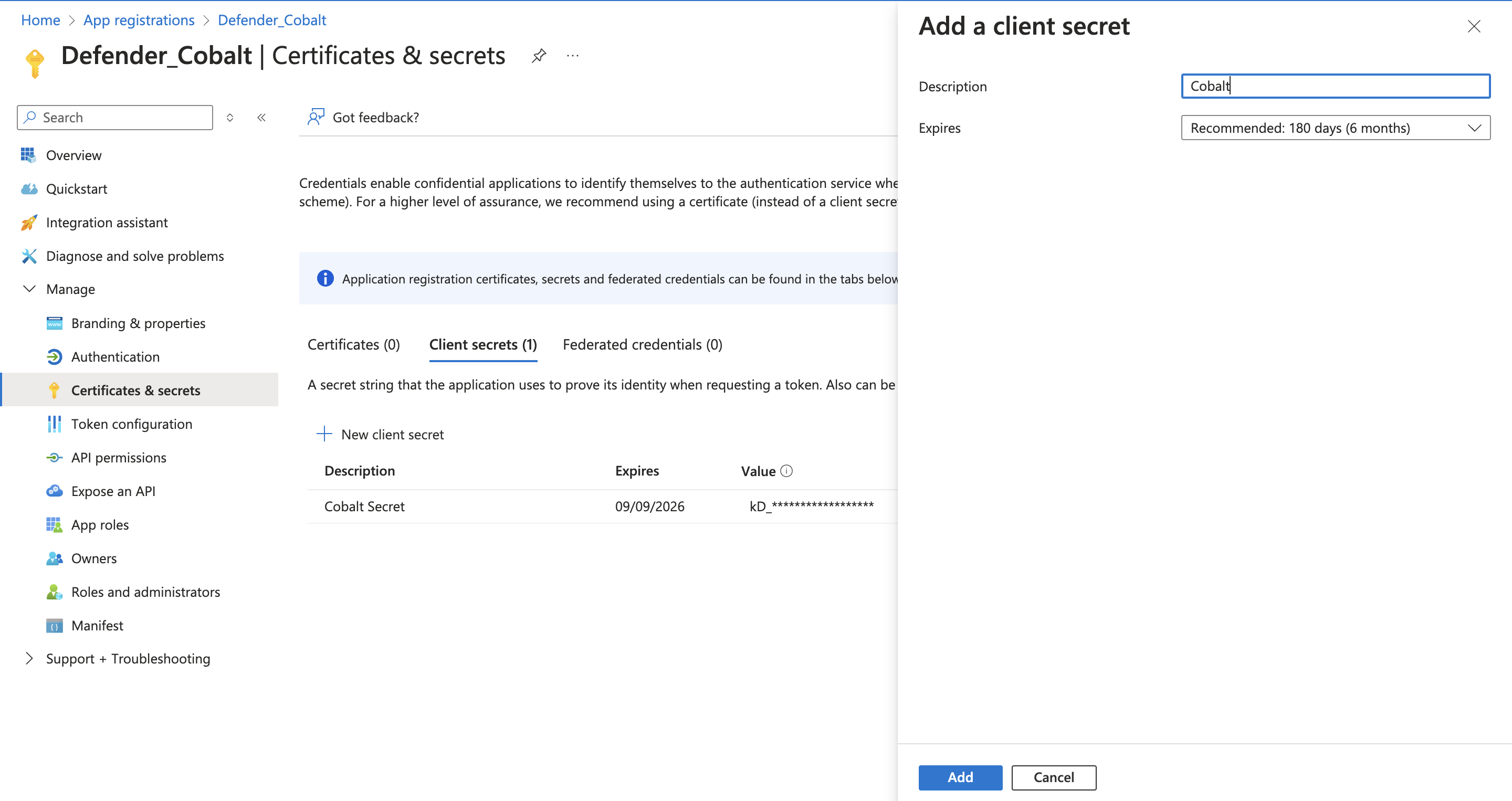
- Navigate to
Certificates and Secretsin the side menu and under Client Secrets tab, press the+ New client secretbutton. Give a Description, select the best expiry for your application and clickAddto create your credentials. - Copy the displayed Client Secret under the
Valuecolumn.

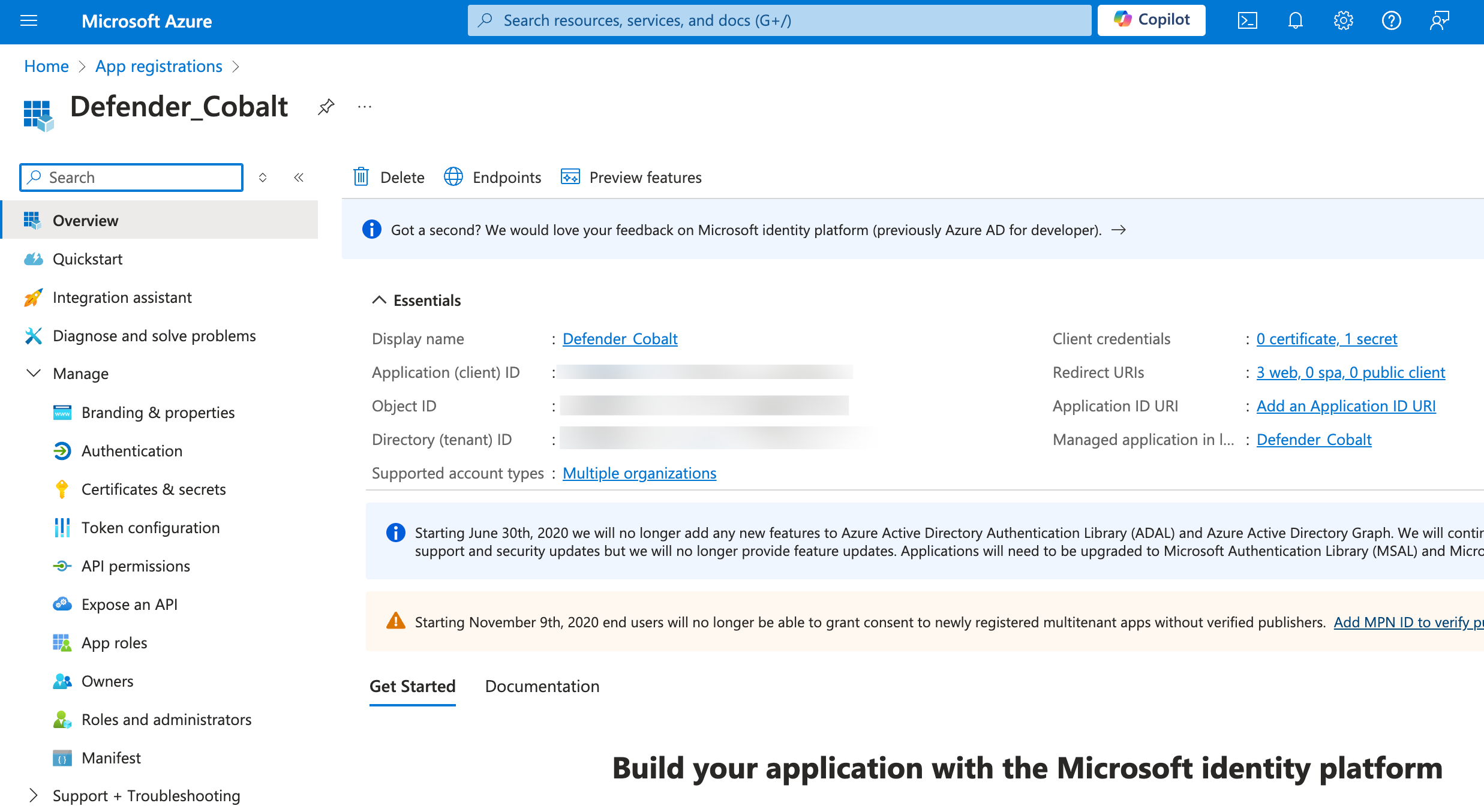
- Navigate to
Overviewin the side menu >Essentialstab > Copy the Client ID underApplication (client) IDand Tenant ID underDirectory (tenant) ID.

Configuring credentials in Cobalt
App settings page lets you configure the authentication settings for anOAuth 2.0 based application. For your customers to provide you authorization to access their data,
they would first need to install your application. This page lets you set up your application credentials.
 Provide the acquired Client ID and Client Secret under Settings of the app and save it.
Provide the acquired Client ID and Client Secret under Settings of the app and save it.
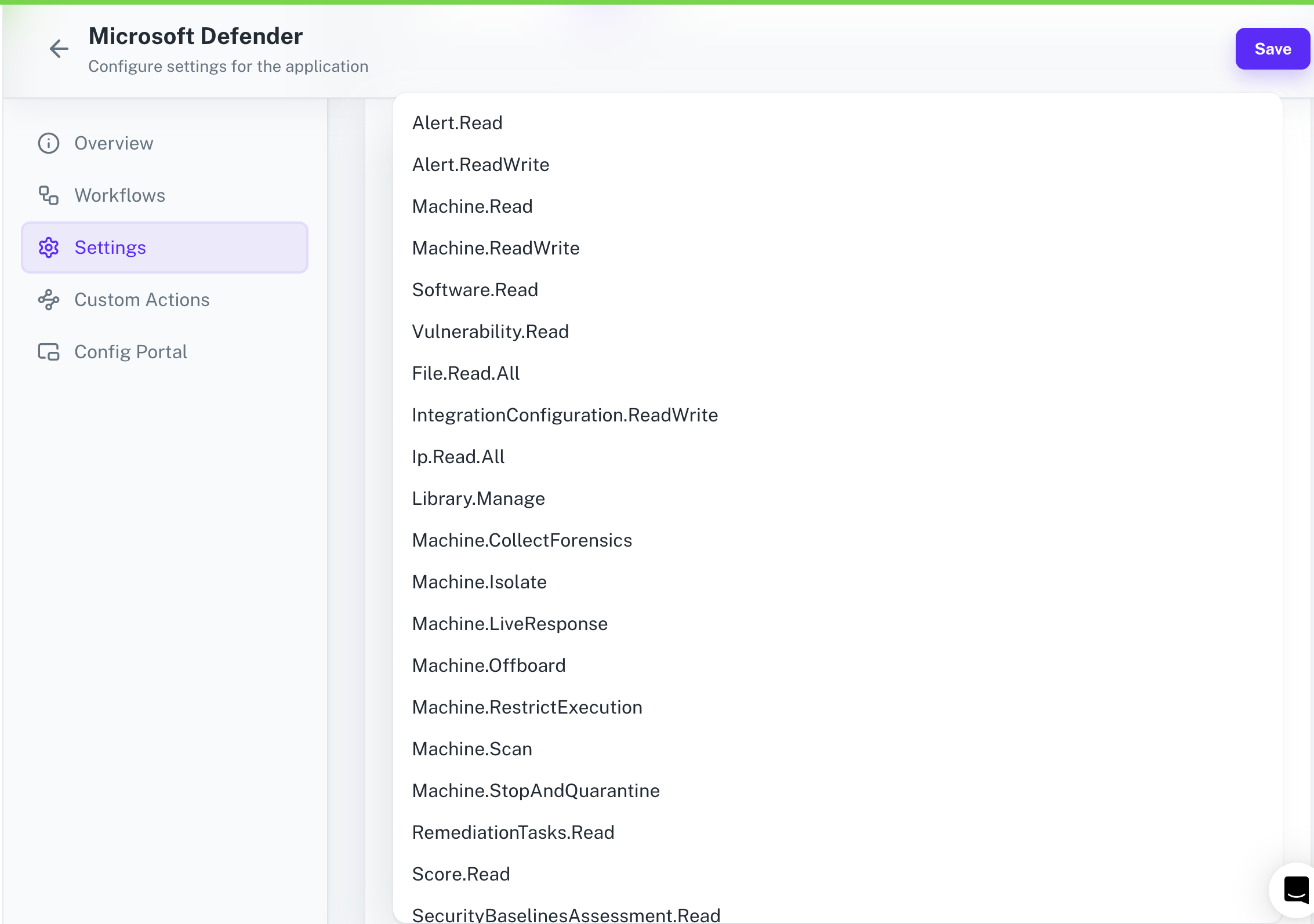
Configuring Scopes
Cobalt lets you configure what permissions to ask from your users while they install your application. The scopes can be added or removed from the App settings page, underPermissions & Scopes
section.
For some applications Cobalt sets mandatory scopes which cannot be removed. Additional scopes can be selected from the drop down. Cobalt also has the provision to add any
custom scopes supported by the respective platform.
 Once the scopes has been added to the application in Cobalt, go to your Microsoft Azure account and update the scopes as added on Cobalt.
Select the OAuth App created for Cobalt and follow Step 8 and 9 above.
Once the scopes has been added to the application in Cobalt, go to your Microsoft Azure account and update the scopes as added on Cobalt.
Select the OAuth App created for Cobalt and follow Step 8 and 9 above.
If you are facing scopes missing or invalid scope error. Make sure you are not passing any custom scope not supported by the platform. And, the scopes selected here are
identical to the ones selected in the platform.
Actions and triggers
Once the above setup is completed, you can create orchestrations of your use-cases using Microsoft Defender actions and triggers. Following are the set of Microsoft Defender actions and triggers supported by Cobalt.Alert
Alert
- List Alerts - Get all alerts in Microsoft Defender.
- Create Alert - Create an alert in your Microsoft Defender.
- Update Alert - Update an alert in your Microsoft Defender.
Machines
Machines
- List Machines - Get all machines in Microsoft Defender.
- Update Machine - Update a machine in Microsoft Defender.
Software
Software
- List Softwares - List all softwares in Microsoft Defender.
- List Machines By Software - List machines by software ID in Microsoft Defender.
Vulnerabilities
Vulnerabilities
- Get All Vulnerabilities - Get all vulnerabilities in Microsoft Defender.
- Get Vulnerability By ID - Get a vulnerability by ID in Microsoft Defender.
- List Vulnerabilities By Machine - Get all vulnerabilities by machine in Microsoft Defender.
- Get Vulnerabilities By Software - Get all vulnerabilities by Software in Microsoft Defender.
Others
Others
- HTTP Request - Make HTTP API calls to any Microsoft Defender documented REST APIs.